Over the last couple of weeks I’ve been working on adapting Function Monkey so that it feels natural to work with in F#. The driver for this is that I find myself writing more and more F# and want to develop the backend for a new app in it and run it on Azure Functions.
I’m not going to pretend its pretty under the covers but its starting to take shape and I’m beginning to use it in my new backend and so now seemed like a good time to write a little about it by walking through putting together a simple ToDo style API that saves data to CosmosDB.
Declaring a Function App
As ever you’ll need to begin by creating a new Azure Function app in the IDE / editor of your choice. Once you’ve got that empty starting point you’ll need to two NuGet package FunctionMonkey.FSharp to the project (either with Paket or Nuget):
FunctionMonkey.FSharp
FunctionMonkey.Compiler
This is currently in alpha and so you’ll need to enable pre-release packages and add the following NuGet repository:
https://www.myget.org/F/functionmonkey-beta/api/v3/index.json
Next by create a new module called EntryPoint that looks like this:
namespace FmFsharpDemo
open AccidentalFish.FSharp.Validation
open System.Security.Claims
open FunctionMonkey.FSharp.Configuration
open FunctionMonkey.FSharp.Models
module EntryPoint =
exception InvalidTokenException
let validateToken (bearerToken:string) =
match bearerToken.Length with
| 0 -> raise InvalidTokenException
| _ -> new ClaimsPrincipal(new ClaimsIdentity([new Claim("userId", "2FF4D861-F9E3-4694-9553-C49A94D7E665")]))
let isResultValid (result:ValidationState) =
match result with
| Ok -> true
| _ -> false
let app = functionApp {
// authorization
defaultAuthorizationMode Token
tokenValidator validateToken
claimsMappings [
claimsMapper.shared ("userId", "userId")
]
// validation
isValid isResultValid
// functions
httpRoute "version" [
azureFunction.http (Handler(getApiVersion), Get)
]
}
Ok. So what’s going on here? We’ll break it down block by block. We’re going to demonstrate authorisation using a (pretend) bearer token and so we begin by creating a function that can validate a token:
exception InvalidTokenException
let validateToken (bearerToken:string) =
match bearerToken.Length with
| 0 -> raise InvalidTokenException
| _ -> new ClaimsPrincipal(new ClaimsIdentity([new Claim("userId", "2FF4D861-F9E3-4694-9553-C49A94D7E665")]))
This is our F# equivalent of the ITokenValidator interface in the C# version. In this case we take valid to mean any string of length in the authorization header and if the token is valid then we return a ClaimsPrincipal. Again here we just return a made up principal. In the case of an invalid token we simply raise an exception – Function Monkey will translate this to a 401 HTTP status.
We’re going to validate the inputs to our functions using my recently released validation framework. Function Monkey for F# supports any validation framework but as such you need to tell it what constitutes a validation failure and so next we create a function that is able to do this:
let isResultValid result = match result with | Ok -> true | _ -> false
Finally we declare our Function App itself:
let app = functionApp {
// authorization
defaultAuthorizationMode Token
tokenValidator validateToken
claimsMappings [
claimsMapper.shared ("userId", "userId")
]
// validation
isValid isResultValid
// functions
httpRoute "version" [
azureFunction.http (Handler(fun () -> "1.0.0"), Get, authorizationMode=Anonymous)
]
}
We declare our settings (and optionally functions) inside a functionApp block that we have to assign to a public member on the module so that the Function Monkey compiler can find your declaration.
Within the block we start by setting up our authorisation to use token validation (line 3) and instruct it to use the token validator function we created earlier (line 4). In lines 5 to 7 we then set up a claims mapping which will set userId on any of our record types associated with functions to the value of the userId claim. You can also set mappings to specific command type property like in the C# version.
On line 9 we tell Function Monkey to use our isResultValid function to determine if a validation results constitutes success of failure.
Then finally on line 11 we declare a HTTP route and a function within it. If you’re familiar with the C# version you can see here that we no longer use commands and command handlers – instead we use functions and their input parameter determines the type of the model being passed into the Azure Function and their return value determines the output of the Azure Function. In this case the function has no parameters and returns a string – a simple API version. We set this specific function to not require authorisation.
Finally lets add a host.json file to remove the auto-prefixing of api to routes (this causes problems with things like Open API output):
{
"version": "2.0",
"extensions": {
"http": {
"routePrefix": ""
}
}
}
If we run this now then in PostMan we should be able go call the endpoint http://localhost:7071/version and receive the response “1.0.0”.
Building our ToDo API
If you’re familiar with Function Monkey for C# then at this point you might be wandering where the rest of the functions are. We could declare them all here like we would in C# but the F# version of Function Monkey allows functions to be declared in multiple modules so that the functions can be located close to the domain logic and to avoid a huge function declaration block.
To get started create a new module called ToDo and we’ll begin by creating a type to model our to do items – we’ll also use this type for updating out to do items:
type ToDoItem =
{
id: string
title: string
complete: bool
}
Next we’ll declare a type for adding a to do item:
type AddToDoItemCommand =
{
userId: string
title: string
isComplete: bool
}
And finally an type that represents querying to find an item:
type GetToDoItemQuery =
{
id: string
}
Next we’ll declare our validations for these models:
let withIdValidations = [
isNotEmpty
hasLengthOf 36
]
let withTitleValidations = [
isNotEmpty
hasMinLengthOf 1
hasMaxLengthOf 255
]
let validateGetToDoItemQuery = createValidatorFor<GetToDoItemQuery>() {
validate (fun q -> q.id) withIdValidations
}
let validateAddToDoItemCommand = createValidatorFor<AddToDoItemCommand>() {
validate (fun c -> c.userId) withIdValidations
validate (fun c -> c.title) withTitleValidations
}
let validateToDoItem = createValidatorFor<ToDoItem>() {
validate (fun c -> c.id) withIdValidations
validate (fun c -> c.title) withTitleValidations
validate (fun c -> c.owningUserId) withIdValidations
}
Ok. So now we need to create functions for adding an item to the database and another for getting one from it. We’ll use Azure CosmosDB as a data store and I’m going to assume you’ve set one up. Our add function needs to accept a record of type AddToDoItemCommand and return a new record of type ToDoItem assigning properties as appropriate:
let addToDoItem command =
{
id = Guid.NewGuid().ToString()
owningUserId = command.userId
title = command.title
isComplete = command.isComplete
}
The user ID on our command will have been populated by the claims binding. We don’t write the item to Cosmos here, instead we’re going to use an output binding shortly.
Next our function for reading a to do item from Cosmos:
let getToDoItem query =
CosmosDb.reader<ToDoItem> <| query.id
CosmosDb.reader is a super simple helper function I created:
namespace FmFsharpDemo
open Microsoft.Azure.Cosmos
open System
module CosmosDb =
let cosmosDatabase = "testdatabase"
let cosmosCollection = "colToDoItems"
let cosmosConnectionString = Environment.GetEnvironmentVariable("cosmosConnectionString")
let reader<'t> id =
async {
use client = new CosmosClient(cosmosConnectionString)
let container = client.GetContainer(cosmosDatabase, cosmosCollection)
let! response = container.ReadItemAsync<'t>(id, new PartitionKey(id)) |> Async.AwaitTask
return response.Resource
}
If we inspect the signatures for our two functions we’ll find that addToDoItem has a signature of AddToDoItemCommand -> ToDoItem and getToDoItem has a signature of GetToDoItemQuery -> Async<ToDoItem>. One of them is asynchronous and the other is not – Function Monkey for F# supports both forms. We’re not going to create a function for updating an existing item to demonstrate handler-less functions (though as we’ll see we’ll duck a slight issue for the time being!).
There is one last step we’re going to take before we declare our functions and that’s to create a curried output binding function:
let todoDatabase =
cosmosDb cosmosCollection cosmosDatabase
In the above cosmosDb is a function that is part of the Function Monkey output binding set and it takes three parameters – the collection / container name, the database name and finally the function that the output binding is being applied to. We’re going to use it multiple times so we create this curried function to make our code less repetitive and more readable.
With all that we can now declare our functions block:
let toDoFunctions = functions {
httpRoute "api/v1/todo" [
azureFunction.http (AsyncHandler(getToDoItem),
verb=Get, subRoute="/{id}",
validator=validateGetToDoItemQuery)
azureFunction.http (Handler(addToDoItem),
verb=Post,
validator=validateAddToDoItemCommand,
returnResponseBodyWithOutputBinding=true)
|> todoDatabase
azureFunction.http (NoHandler, verb=Put, validator=validateToDoItem)
|> todoDatabase
]
}
The functions block is a subset of the functionApp block we saw earlier and can only be used to define functions – shared configuration must go in the functionApp block.
Hopefully the first, GET verb, function is reasonably self-explanatory. The AsyncHandler case instructs Function Monkey that this is an async function and we assign a validator with the validator option.
The second function, for our POST verb, introduces a new concept – output bindings. We pipe the output of azureFunction.http to our curried output binding and this will result in a function being created that outputs to Cosmos DB. Because we’re using the Cosmos output binding we also need to add the Microsoft.Azure.WebJobs.Extensions.CosmosDB package to our functional project. We set the option returnResponseBodyWithOutputBinding to true so that as well as sending the output of our function to the output trigger we also return it as part of the HTTP response (this is optional as you can imagine in a more complex scenario that could leak data).
Finally for the third function our PUT verb also uses an output binding but this doesn’t have a handler at all, hence the NoHandler case. In this scenario the command that is passed in, once validated, is simply passed on as the output of the function. And so in this instance we can PUT a to do item to our endpoint and it will update the appropriate entry in Cosmos. (Note that for the moment I have not answered the question as to how to prevent one user from updating another users to do items – our authorisation approach is currently limited and I’ll come back to that in a future post).
Trying It Out
With all that done we can try this function app out in Postman. If we begin by attempting to add an invalid post to our POST endpoint, say with an empty title, we’ll get a 400 status code returned and a response as follows:
{
"case": "Errors",
"fields": [
[
{
"message": "Must not be empty",
"property": "title",
"errorCode": "isNotEmpty"
},
{
"message": "Must have a length no less than 1",
"property": "title",
"errorCode": "hasMinLengthOf"
}
]
]
}
Now if we run it with a valid payload we will get:
{
"id": "09482e8d-41aa-4c25-9552-b7b05bf0a787",
"owningUserId": "2FF4D861-F9E3-4694-9553-C49A94D7E665",
"title": "Buy underpants",
"isComplete": false
}
Next Steps
These are with me really – I need to continue to flesh out the functionality which at this point essentially boils down to expanding out the computation expression and its helpers. I also need to spend some time refactoring aspects of Function Monkey. I’ve had to dig up and change quite a few things so that it can work in this more functional manner as well as continue to support the more typical C# patterns.
Then of course there is documentation!


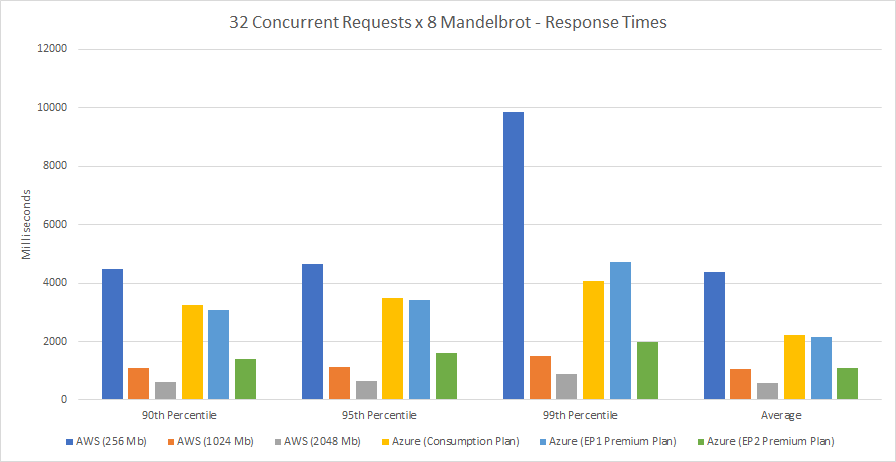
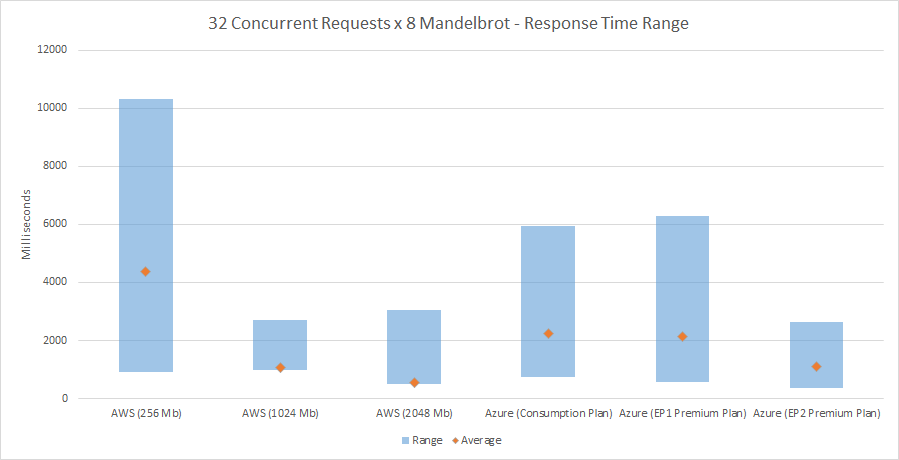
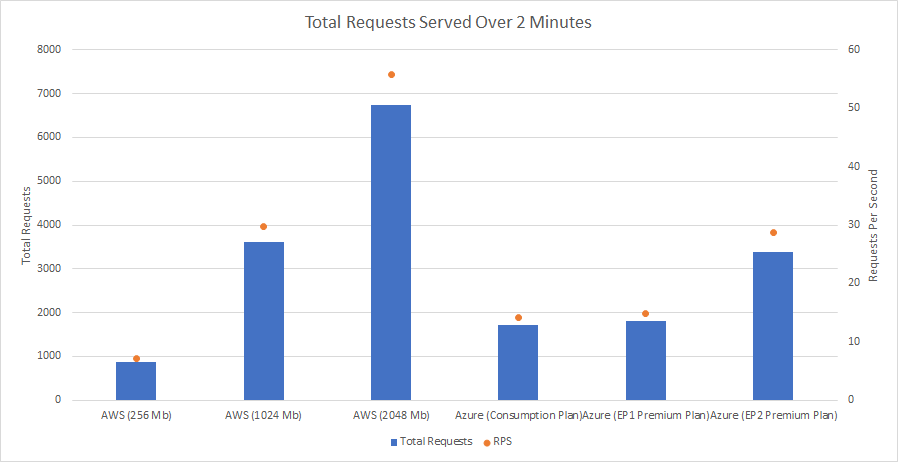
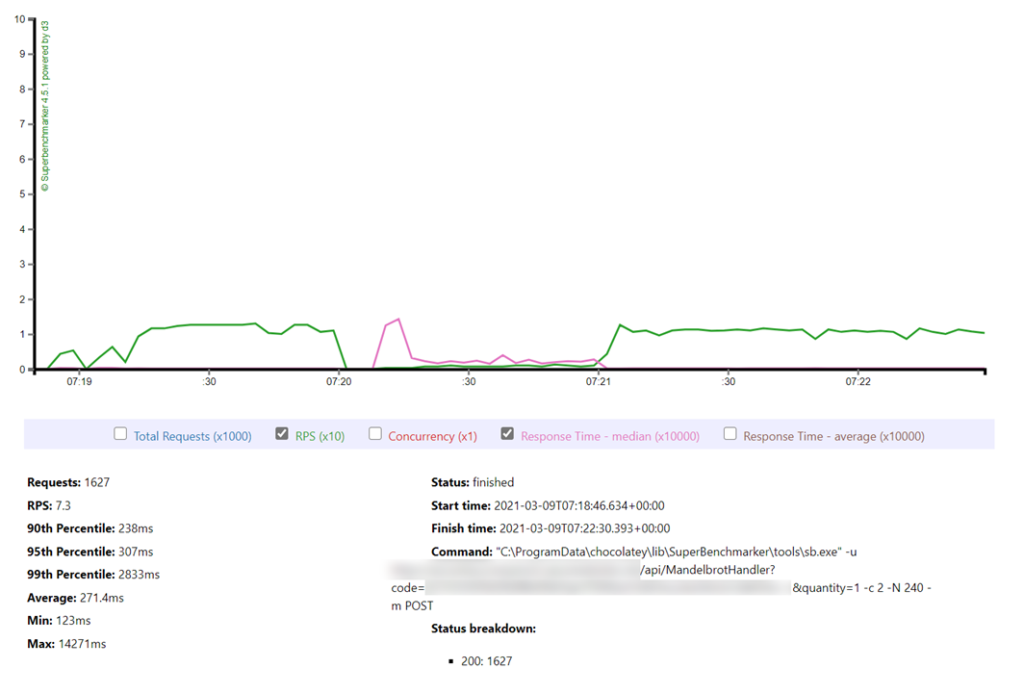



Recent Comments